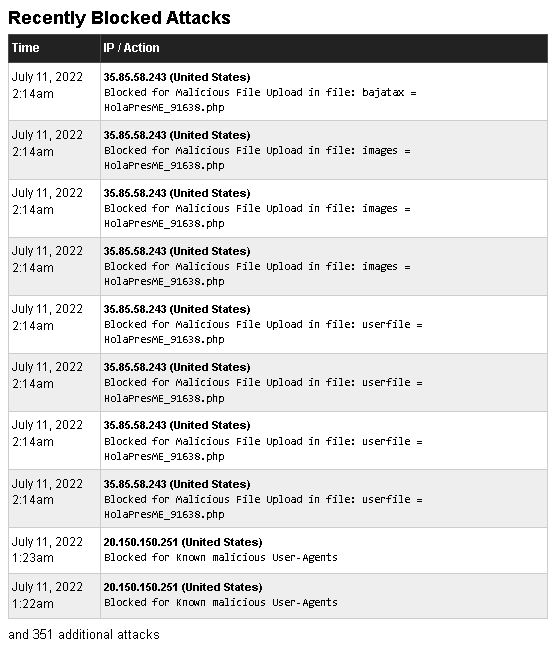
One is Portland the other is Phoenix, but they could have bounced in from anywhere. There’s also no way to tell if these are just routine scumbag predators or if these are directed agenda-driven attacks. And no, I don’t know what that file is.
Either way, some people sure are @$$holes.
And ditto for anyone who can’t be trusted with a keyboard…


The abusers are using Amazon and Microsoft hosting services, meaning they could actually be anywhere.
Send a copy of the appropriate log entries to abuse@amazonaws.com and abuse@microsoft.com and get them booted.
From the Amazon WHOIS listing:
Comment: All abuse reports MUST include:
Comment: * src IP
Comment: * dest IP (your IP)
Comment: * dest port
Comment: * Accurate date/timestamp and timezone of activity
Comment: * Intensity/frequency (short log extracts)
Comment: * Your contact details (phone and email) Without these we will be unable to identify the correct owner of the IP address at that point in time.