Received via email:
The Wordfence Web Application Firewall has blocked 266 attacks over the last 10 minutes. Wordfence is blocking these attacks, and we’re sending this notice to make you aware that there is a higher volume of the attacks than usual.
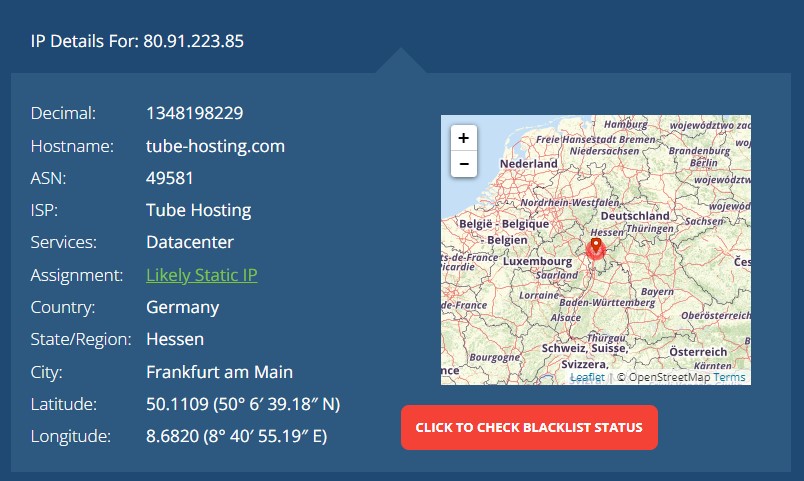
F*** y0u, @$$hole in Germany.
I tried to check out Tube-Hosting but got a “badware” warning so I backed out.


If they’re using a VPN, they could be anyplace.
https://helpcenter.trendmicro.com/en-us/article/tmka-11327
I use PIA (Private Internet Access) but they all do something similar. When one connects to their VPN app, their internet traffic is encrypted in addition to the encryption done on an https link, so that someone listening in cannot see what they’re doing. When connecting to the app one also selects one of literally dozens if not hundreds of “exit routers” that can be placed anywhere in the world. If someone is listening in they see the traffic as originating from the IP address of that router, not the IP address of the user. in this way, someone can mask where they are as well as what they’re doing.
A similar technique involves the TOR (The Onion Router) protocol developed by the U S Navy. One connects to a TOR “edge router” which encrypts their traffic and hands it off to a randomly selected TOR “node router.” That “node router” decrypts what it receives, reencrypts it and hands it off to another “node router.” After a random number of hops through the TOR router mesh, the traffic is handed off to another randomly selected “edge router” and then off to its intended destination. In this case, someone attempting to monitor the traffic sees it as originating from that second “edge router”, as opposed to the originator’s location.
https://en.wikipedia.org/wiki/Tor_(network)
Long story short, the person attacking your site could be in Germany, but if they’re sharp, they could be anywhere.
It’s possible that the cyberattacker is someplace else. I have seen Tor used to fake an ISP location ion Switzerland when the real location was North Carolina. Maybe one of your readers with more computer savvy than me can explain how this works.